Attackers have been quick to exploit the Shellshock Bash command interpreter bug disclosed yesterday by building a botnet that is currently trying to infect other servers, according to a security researcher.
The "wopbot" botnet is active and scanning the internet for vulnerable systems, including at the United States Department of Defence, chief executive of Italian security consultancy Tiger Security, Emanuele Gentili, told iTnews.
"We have found a botnet that runs on Linux servers, named “wopbot", that uses the Bash Shellshock bug to auto-infect other servers," Gentili said.
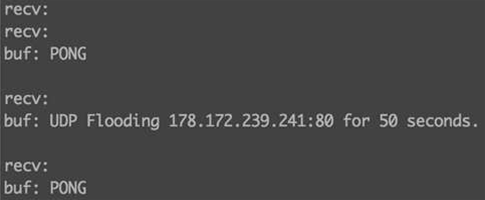
Wopbot has so far launched a distributed denial of service attack against servers hosted by content delivery network Akamai, and is also aiming for other targets, according to Gentili.
"Analysing the malware sample in a sandbox, we saw that the malware has conducted a massive scan on the United States Department of Defence Internet Protocol address range on port 23 TCP or Telnet for brute force attack purposes," he said.
The US DoD network in question is the 215.0.0.0/8 range, with approximately 16.7 million addresses.
Gentili said Tiger Security had contacted UK provider M247 and managed to get the wopbot botnet command and control system taken down from that network.
However, the botmaster server for wopbot - hosted by US network Datawagon - is still up and distributing malware, Gentili said.
He was unable to say how many systems are involved in the wopbot botnet, but he believes the number could increase very fast.
"Unfortunately is not easy for us say how many servers has been infected, but in the past I observed that similar botnets were able to infect more than 200,000 zombies in an hour or so," Gentili said.
The 'Shellshock' remotely exploitable vulnerability in the Bash Linux command-line shell was discovered yesterday, with researchers warning of its potential to become larger than the severe Heartbleed OpenSSL flaw uncovered earlier this year.
Millions of Apache webservers around the world could be at risk if their common gateway interface (CGI) scripts invoke Bash.